With sophisticated cyberattacks on the rise, businesses of all sizes need extensive security solutions to secure their endpoints and enable swift incident response. Any solutions provider in need of endpoint detection and response (EDR) tools today should consider those that deliver real-time protection and automated threat mitigation. We explore some of the top EDR tools available based on key factors such as core features, AI-driven capabilities, ease of use, and more.
What is EDR and who should use it?
EDR tools are frontline defense for endpoint security as they are software tools that combine real-time monitoring, data collection, and analysis to detect, investigate, and mitigate security incidents. These tools provide visibility into endpoint activities and enable IT teams to isolate compromised systems, remediate threats, and prevent future attacks.
If you’re a solutions provider or MSP that manages networks across multiple client environments, especially in industries that handle sensitive data, like healthcare, finance, or government sectors, you should consider EDR tools. Businesses experiencing a high volume of remote or hybrid work will benefit from the heightened endpoint visibility and security offered by EDR tools. Additionally, MSPs looking to enhance their security offerings should consider EDR as the foundation of their managed security services portfolio.
- CrowdStrike: Best overall for pricing and intuitiveness
- Rapid7: Best EDR solution for real-time analytics
- SentinelOne: Best for AI-powered threat protection
- IBM: Best solution for enterprise-scale EDR
- Trend Micro: Best for advanced features and compatibility
- Syxsense: Best EDR tool for responsive support
Featured Partners: Endpoint Detection and Response (EDR) Software
Top EDR tools comparison
See how the top tools compare across their top features and starting prices.
| Tool | Starting Price | Vulnerability Management | Forensic Analysis | Endpoint Visibility | Cross-platform Support | Sandboxing |
|---|---|---|---|---|---|---|
| CrowdStrike | $59.99/device | ✔ | ✔ | ✔ | — | ✔ |
| Rapid7 | $3.82/asset/month | ✔ | — | ✔ | ✔ | — |
| SentinelOne | $69.99/endpoint for 5-100 endpoints | ✔ | ✔ | ✔ | — | ✔ |
| IBM | $303/month for 100+ endpoints | ✔ | ✔ | ✔ | ✔ | — |
| Trend Micro | Custom | ✔ | ✔ | ✔ | ✔ | ✔ |
| Syxsense | Custom | ✔ | — | ✔ | ✔ | — |
✔=Yes —= Limited

CrowdStrike
Best overall for pricing and intuitiveness
Overall rating: 4.3/5
- Cost: 4.6/5
- Core features: 4.5/5
- Customer support: 4.5/5
- Ease of use: 4.6/5
- AI-driven threat detection: 4.5/5
- Integration and compatibility: 4/5
CrowdStrike Falcon is our top endpoint detection and response (EDR) pick, known for its cloud-native architecture, ease of deployment, and advanced threat intelligence. With a simple, intuitive interface, its variety of pricing options and consideration for businesses of all sizes enhance its popularity. The platform offers flexible pricing plans that suit both small businesses and large enterprises. It also offers seamless cross-platform compatibility and advanced forensic analysis tools.
| Pros | Cons |
|---|---|
| Intuitive, user-friendly interface | Higher starting price than some competitors |
| AI-powered real-time threat detection | Lacks advanced reporting in the basic package |
| Strong cross-platform support | Higher tiers require contacting sales for pricing |
| Comprehensive forensic analysis | Limited support for smaller enterprises’ customizations |
Pricing
- Falcon Go: $59.99 per device annually for a maximum of 100 devices
- Falcon Pro: $99.99 per device annually
- Falcon Enterprise: $184.99 per device annually
- Falcon Elite: Contact for quote
- Falcon Complete MDR: Contact for quote
Features
- AI-powered real-time threat detection: Provide real-time threat detection with low false positives using Falcon’s AI analytics.
- Automated incident response: Offer seamless response workflows with minimal manual input.
- Advanced forensic tools: Deliver in-depth root cause analysis and historical attack chain visualization enable detailed forensics.
- Custom detection rules: Customize detection rules to meet specific security needs of your users.
Who should use CrowdStrike?
Providers that need a cost-effective and easy to deploy solution for endpoint security. Its modular pricing allows organizations to scale their security stack based on current needs, which makes it a great fit for growing businesses or companies with evolving requirements.
Who should not use it?
Organizations that need extensive analytics and reporting out of the box may find the basic tiers insufficient. For a more comprehensive solution with advanced analytics, Rapid7 is a stronger alternative. It provides deeper threat insights and detailed reporting.

Rapid7
Best for real-time analytics
Overall rating: 3.9/5
- Cost: 3.7/5
- Core features: 3.9/5
- Customer support: 4.2/5
- Ease of use: 3.7/5
- Real-time analytics: 4.2/5
- Integration and compatibility: 4.3/5
Rapid7’s InsightIDR is known for its strong focus on real-time analytics, providing quick threat detection and incident response. User and entity behavior analytics (UEBA) and network traffic analysis, ensuring security teams can identify and address threats rapidly. Rapid7 also has extensive EDR features, which is a win for any organization that needs to improve their incident response times as well as in-depth, real-time insights into potential risks and effectively managing diverse environments.
| Pros | Cons |
|---|---|
| Powerful real-time threat detection | Limited reporting in lower-tier plans |
| Excellent integration with third-party tools | Can be complex for smaller teams |
| Advanced user and entity behavior analytics | Higher price for smaller teams |
| Robust SIEM capabilities | Requires a learning curve for full feature usage |
Pricing
For environments with 250k assets:
- Essential: Begins at $3.82 per asset per month.
- Advanced: Starts at $6.36 per asset per month.
- Ultimate: begins at $8.21 per asset per month.
Features
- SIEM and EDR: Provide full SIEM capabilities combined with advanced endpoint detection.
- Network traffic analysis: Offer network visibility, intrusion detection, and data forensics for comprehensive threat insights.
- User and entity behavior analytics (UEBA): Continuously track and analyze user behavior to detect anomalies.
- Deception technology: Include decoy systems and traps to proactively identify and mitigate attackers.
Who should use Rapid7?
Rapid7 is best for businesses looking for a mix of advanced real-time analytics and high-level threat detection capabilities. Organizations that need deep user behavior analytics and continuous network monitoring will appreciate this tool.
Who should not use Rapid7?
Organizations that prioritize more straightforward setup and extensive out-of-the-box reporting might find Rapid7’s InsightIDR to be rather challenging. For those focused on ease of use and simplicity, CrowdStrike would be a more natural alternative as it’s user-friendly and offers robust support.

SentinelOne
Best for AI-powered threat protection
Overall rating: 3.9/5
- Cost: 3.4/5
- Core features: 4.3/5
- Customer support: 3.5/5
- Ease of use: 4.2/5
- AI capabilities: 4.7/5
- Integration and compatibility: 3.8/5
SentinelOne excels in AI-driven threat protection, offering fully autonomous endpoint protection with ActiveEDR. Its Singularity platform provides powerful behavioral AI capabilities that continuously analyze and respond to threats in real-time. This automation minimizes the need for manual intervention. With the ability to predict, prevent, and remediate attacks autonomously, SentinelOne’s offering is strong enough to sway teams seeking cutting-edge AI technology to bolster their security.
| Pros | Cons |
|---|---|
| Autonomous AI-driven threat detection and response | Has no free trial |
| Real-time analytics and incident response | Learning curve for small teams |
| Comprehensive OS support | Complex setup for some features |
| AI-powered forensics and behavioral analytics | Limited customization for entry-level plans |
Pricing
For 5-100 workstations:
- Singularity Core: $69.99 per endpoint
- Singularity Control: $79.99 per endpoint
- Singularity Complete: $159.99 per endpoint
- Singularity Commercial: $209.99 per endpoint
- Singularity Enterprise: Contact for quote
Features
- AI-powered threat detection: Automatically detect zero-day and advanced threats using deep learning AI models.
- ActiveEDR: Automate detection, response, and remediation using real-time AI-based tools.
- Threat hunting: Proactively seek out threats using SentinelOne’s behavioral AI analytics.
- Advanced forensics: Visualize and investigate incidents with a detailed root cause analysis and attack chain visualization.
Who should use SentinelOne?
SentinelOne is ideal for organizations that need autonomous, AI-powered threat detection in place of manual security operations. It’s worth considering for anyone who wants AI capabilities to predict and respond to cyber threats without human intervention.
Who should not use SentinelOne?
Businesses that need a simpler, more intuitive setup and a cost-effective solution may gravitate towards Rapid7, as it offers strong analytics without the higher complexity and cost associated with advanced AI-powered platforms like SentinelOne.

IBM QRadar
Best for enterprise-scale EDR
Overall rating: 3.8/5
- Cost: 2.7/5
- Core features: 4.3/5
- Customer support: 4.3/5
- Ease of use: 2.9/5
- AI capabilities: 4.7/5
- Integration and compatibility: 3.8/5
IBM QRadar excels in offering an enterprise-scale EDR solution for handling complex environments. With its integration into the broader IBM QRadar Security Information and Event Management (SIEM) ecosystem, it delivers in-depth threat detection, investigation, and response across hybrid environments. QRadar is capable of managing massive volumes of security data and offering automated workflows. The platform leverages AI and machine learning through its Cyber Assistant, which autonomously manages alerts and reduces false positives.
| Pros | Cons |
|---|---|
| Powerful integration with SIEM and SOAR | Higher cost for smaller businesses |
| Scalable for large environments | Steep learning curve for beginners |
| Advanced threat detection capabilities | Complex setup process |
| Customizable AI-based analytics | Requires experienced security staff |
Pricing
IBM QRadar EDR offers scalable pricing based on the number of endpoints. It offers a pricing calculator on its website whose minimum of 100 endpoints are estimated to cost $303 monthly and $3633 annually.
Features
- Cyber Assistant: Offer your users AI-powered alert management, reduce false positives, and enhance the efficiency of analysts.
- Custom detection strategies: Enable businesses to build and implement tailored detection models to meet compliance needs.
- Ransomware prevention: Offer advanced protection to organizations and enable them to detect and prevent ransomware attacks in near real-time.
- Behavioral tree: Provide full attack visibility and visual storylines to aid analysts in fast triaging, response, and incident containment.
Who should use IBM QRadar?
IBM QRadar is perfect for large enterprises with complex security environments that need a highly scalable EDR solution. It offers extensive integration with other IBM security tools, appealing greatly to organizations that are in need of an all-encompassing security ecosystem.
Who should not use IBM QRadar?
Small to mid-sized businesses with simpler security needs may find the complexity of QRadar prohibitive. A more intuitive option for smaller businesses would be CrowdStrike, as it has packages specifically for small and mid-sized businesses.

Trend Micro
Best for advanced features and compatibility
Overall rating: 3.7/5
- Cost: 1.5/5
- Core features: 4.5/5
- Customer support: 2.3/5
- Ease of use: 4.3/5
- AI capabilities: 4.5/5
- Integration and compatibility: 4.5/5
Trend Micro offers a thorough EDR solution designed to provide advanced threat protection and automated detection capabilities. The platform is equipped with tools such as advanced machine learning and behavioral analysis to detect threats across all endpoints in real-time. Trend Micro also performs well in forensic analysis, providing a rich set of features to investigate the root cause of attacks while supporting proactive threat hunting. It also delivers deep integration with cloud services and the ability to scale across large enterprises.
| Pros | Cons |
|---|---|
| Advanced AI-based threat detection | Opaque pricing |
| Strong cloud and enterprise integration | Limited visibility in smaller deployments |
| Comprehensive forensic and root cause analysis | Some features require manual configuration |
| Proactive threat-hunting capabilities | Initial setup can be complex |
Pricing
Contact for specific pricing information as pricing isn’t listed publicly.
Features
- Advanced machine learning: Leverage AI and machine learning algorithms to detect and prevent advanced threats across all endpoints.
- Behavioral analysis: Provide continuous monitoring of endpoint activities to identify potential attacks based on anomalous behavior.
- Forensic tools: Use deep forensic capabilities to investigate and determine the root cause of cyber incidents.
- Proactive threat hunting: Supports manual and automated threat hunting across enterprise networks.
- Cloud integration: Deliver seamless integration with cloud services for users in hybrid environments.
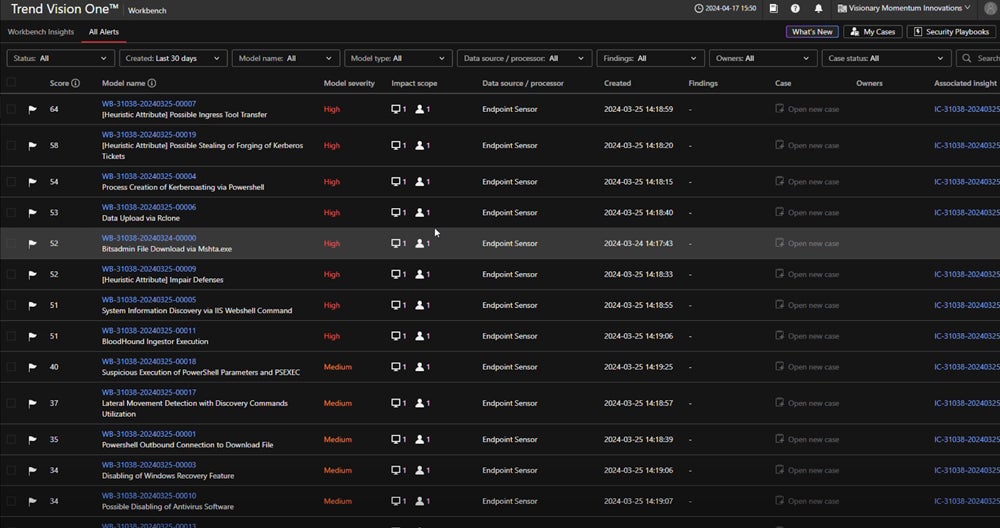
Who should use Trend Micro?
If you consider advanced security features and deep integration capabilities as priorities, Trend Micro should top your shortlist. Additionally, businesses in highly regulated industries, such as healthcare and finance, will benefit from Trend Micro’s compliance management tools.
Who should not use Trend Micro?
Smaller organizations or those that want simplified security solutions with minimal configuration may feel overwhelmed by Trend Micro’s advanced features and integrations. For those looking for a more user-friendly platform without extensive manual setup or integration complexities, SentinelOne, known for its intuitive interface and AI-based threat detection, would be a better fit.

Syxsense
Best for responsive support
Overall rating: 3.7/5
- Cost: 2.9/5
- Core features: 4/5
- Customer support: 4.8/5
- Ease of use: 3.8/5
- AI capabilities: 3/5
- Integration and compatibility: 3.8/5
Syxsense provides a unified endpoint and vulnerability management platform that stands out for its responsive support, offering multi-channel assistance that covers email, live chat, and dedicated phone support. Its customers benefit from strong onboarding and training, and its simplified user interface, comprehensive documentation, and a dedicated customer support team further enhance the user experience and make it easier for users to resolve issues quickly.
| Pros | Cons |
|---|---|
| Unified security and endpoint management console | AI-based analytics are less advanced |
| Strong customer support and onboarding assistance | Can be costly for larger-scale deployments |
| Real-time vulnerability and patch management | Fewer third-party integrations |
| Intuitive user interface | Opaque pricing |
Pricing
Syxsense encourages prospective customers to contact them for a quote.
Features
- Patch management automation: Automate patch updates across devices, ensuring systems remain up-to-date.
- Automated endpoint management: Provide comprehensive IT asset discovery, patch management, and feature updates.
- Syxsense Cortex: Enable no-code automation and orchestration to manage and remediate security threats efficiently.
- Zero trust security: Implement continuous, real-time security controls and vulnerability assessments for all endpoints.
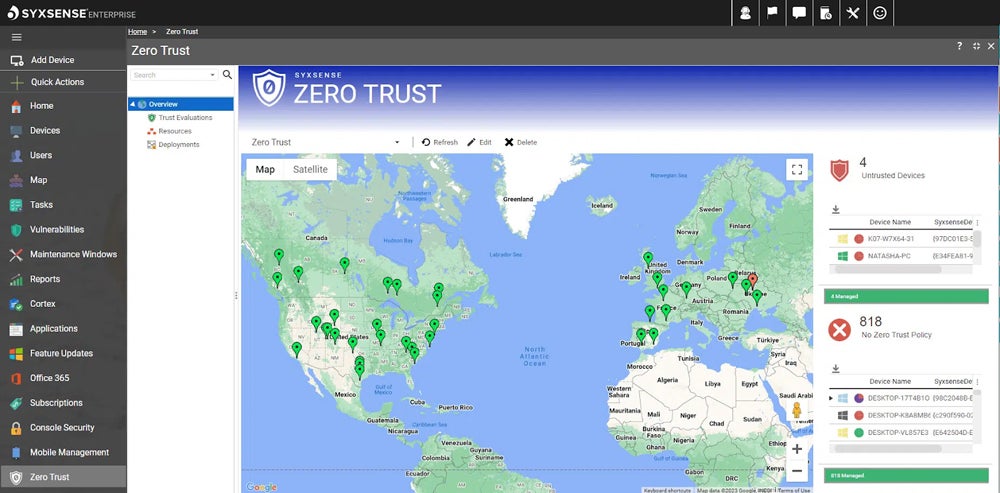
Who should use Syxsense?
Syxsense is a worthy consideration for mid-sized organizations prioritizing responsive support and all-rounded support. Teams that require hands-on assistance and a simple yet effective platform will benefit from Syxsense’s customer-first approach.
Who should not use Syxsense?
Larger enterprises with more complex security environments may find Syxsense’s feature set and AI capabilities rather limited. In this case, IBM QRadar offers a more scalable and feature-rich EDR solution tailored to enterprise needs.
How to choose EDR tools
Selecting the right EDR tool varies based on your needs, however, some of the common factors to consider include:
- Capabilities: EDR tools need to offer comprehensive threat detection, real-time monitoring, and behavioral analytics. Solutions like SentinelOne, IBM, and Trend Micro lead in providing advanced detection mechanisms.
- Scalability: Organizations with larger or expanding infrastructures have scalability high up in their lists. IBM excels at supporting enterprise-level deployments with robust integration into larger IT environments.
- Integration capabilities: For businesses with established security stacks, compatibility is key. Trend Micro is particularly strong in this area, with extensive third-party integrations.
- Cost: The pricing structure is a major consideration for any business. CrowdStrike is notable for its flexible pricing tiers that make it accessible to businesses of all sizes.
- Ease of use: Ease of navigation and user-friendly dashboards are crucial for efficient security operations. A highly intuitive interface makes it easier for teams to quickly respond to threats.
- Customer support: Shortlist solutions that not only deliver your preferred support methods, but also have these methods rated highly by other customers.
Methodology
To identify the best endpoint detection and response tools, we evaluated each platform based on six weighted scoring categories, each with a maximum of five points. The highest scoring tool per category automatically became the criterion winner, and the solution with the best overall average across these categories was chosen as our overall winner.
We gave core features the highest weight as functionality directly affects the platform’s ability to protect, detect, and respond to security incidents, followed by cost as purchasing power determines the kind of tool you can get. This was followed by AI capabilities, customer support, and integration and compatibility, with ease of use completing the list.
- Core Features (25%): We evaluated essential features such as real-time threat detection, vulnerability management, forensic analysis, endpoint visibility, and zero-day threat protection.
- Criterion winner: Trend Micro.
- AI capabilities (20%): This category assessed how well each tool incorporates AI-driven capabilities, including threat detection, automated triage, risk scoring, and real-time behavioral analysis.
- Criterion winner: Multiple winners.
- Cost (20%): We considered pricing transparency, the availability of free trials or demos, and the flexibility of pricing plans, including any hidden costs associated with integrations or advanced features.
- Criterion winner: CrowdStrike.
- Customer support (15%): This category assessed the availability and quality of customer support channels such as live chat, phone, and email. We also considered user feedback to gauge responsiveness and the quality of service.
- Criterion winner: Syxsense.
- Integration and compatibility (15%): This category focused on each platform’s ability to integrate with third-party tools (such as SIEM and SOAR), API support, cross-platform compatibility, and custom connectors.
- Criterion winner: Trend Micro.
- Ease of use (10%): We evaluated how intuitive and user-friendly the platform is, considering aspects such as setup, navigation, and the availability of resources like knowledge bases.
- Criterion winner: CrowdStrike.
Bottom line: Need for advanced EDR solutions
For MSPs considering evolving into MSSPs, integrating effective EDR tools becomes critical to handle the growing complexity of cyber threats, especially in the face of increased ransomware and zero-day attacks. Each tool we’ve reviewed provides unique features, from AI-powered threat protection to real-time analytics, designed to approach endpoint security based on your use case. By determining the right solution, you can ensure you meet the security demands of your clients and keep your services competitive.
Frequently asked questions (FAQs)
What are EDR and XDR tools?
EDR (Endpoint Detection and Response) focuses on detecting, investigating, and responding to threats on endpoints such as computers and mobile devices. XDR (Extended Detection and Response) expands this by integrating data from multiple security layers, including endpoints, networks, and servers, for broader threat visibility.
What is the best EDR?
Although the best EDR tool is dependent on your needs and use case, some of the top EDR solutions include CrowdStrike for its pricing and scalability, SentinelOne for its AI-powered threat protection, and IBM for its robust enterprise-scale capabilities. Each tool excels in different areas, making them suitable for varying business needs.


